For more than a century, the question of who first set foot in the Americas — and how they arrived…
Scientists Discover How “Standing Straighter” Let Ancient Reptiles Become Giants
Long before dinosaurs thundered across prehistoric floodplains, the ancestors of crocodiles, birds and other archosaurs faced a problem written not…
Dinosaur With “Future” Anatomy Found 231 Million Years Too Early — Scientists Stunned
For more than a century, paleontologists pictured the earliest dinosaurs as few, simple, and primitive — a tentative beginning before…
Dinosaurs Were Not Dying Out — They Were Thriving Until the Sky Fell
For decades, the story of the dinosaurs’ end was told with a quiet inevitability. Textbooks, documentaries, and museum displays painted…
Florida’s Signature Corals Just Went “Functionally Extinct” — Scientists Say This Is the Warning the World Ignored
In the summer of 2023, the water off Florida was not merely warm — it was lethal. Divers descending into…
66-Million-Year-Old Clay Mask Reveals First Realistic Full-Body Portrait of a Giant Dinosaur
Sixty-six million years ago, in the waning days before an asteroid erased the dinosaurs, a duck-billed giant died beside a…
Astronomers Found a “Hidden Galaxy” Inside the Milky Way — And It Changes Everything We Thought About Star Birth
The Milky Way is alive with motion, light, and mystery. Among its spiral arms, vast clouds of gas and dust…
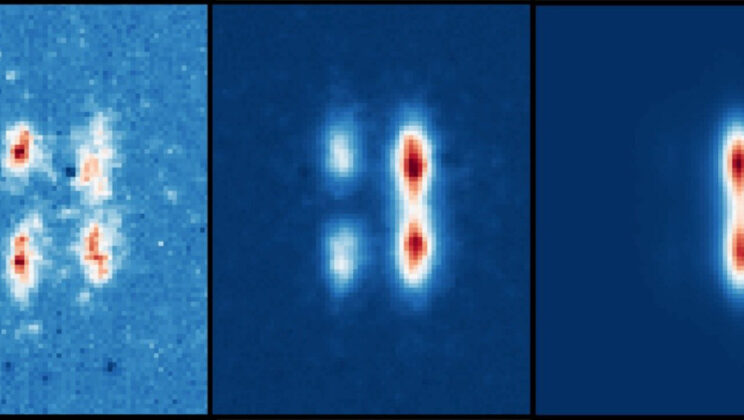
Physicists May Have Discovered an Entirely New State of Matter — And It Forms at the Coldest Temperatures in the Universe
There is a regime of nature in which motion stops matter from revealing what it is. Most of the time,…
Scientists Spin a “Quantum Paradox” — Supersolid Starts Dancing in Sync Under Rotation
Most states of matter obey a kind of loyalty: a solid holds shape, a fluid flows, and a superfluid flows…
Physicists Catch Photons “Choosing Sides” — Light Particles Seen Following the Crowd for the First Time
If photons could speak, they would not tell stories of heroism or independence. They would talk about consensus. Unlike the…
Scientists Can Now “Weigh” Every Grain of Sand in a Dune — Using Only a Photo and AI
For as long as people have watched sand move—underfoot in a desert, under waves in the sea, or in satellite…
The Planet’s “Hidden Climate Shield” May Flip — And Start Heating the World Instead
Peatlands do not look like climate engines. They are quiet places — soggy moss beds, slow-dripping swamps, spruce bogs that…
Scientists Crack Mount Etna’s “Secret Code” for Predicting Eruptions Months in Advance
Mount Etna does not sneak up on people. It looms — a massive, black-walled reminder on the skyline of Sicily…
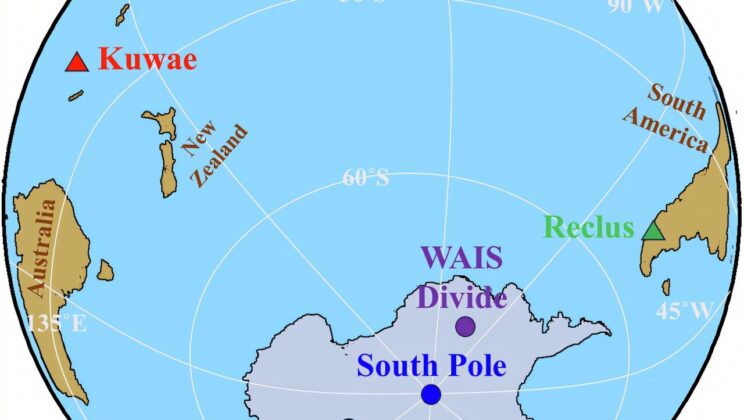
Scientists Discover the 1458 “Volcanic Double Punch” That Silently Cooled Earth for Decades
Nearly six centuries ago, long before satellites or thermometers, the world suddenly chilled. Tree rings stopped widening. Glaciers crept forward.…
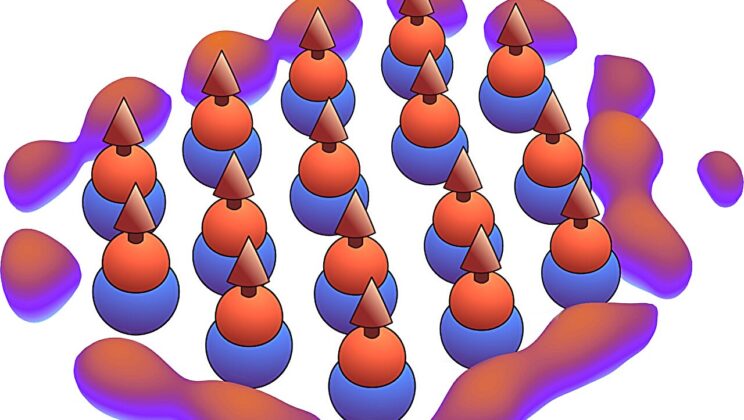
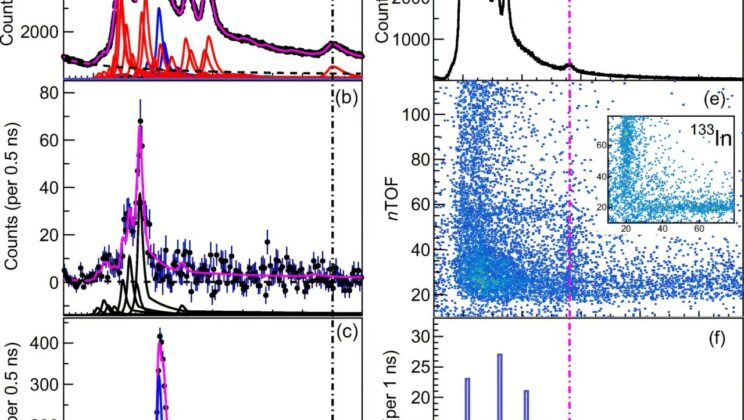
Scientists Crack the Nuclear Code Behind Gold’s Cosmic Birth for the First Time
You cannot wear gold unless a nucleus somewhere, some time, decayed. That fact alone should alter the way we look…
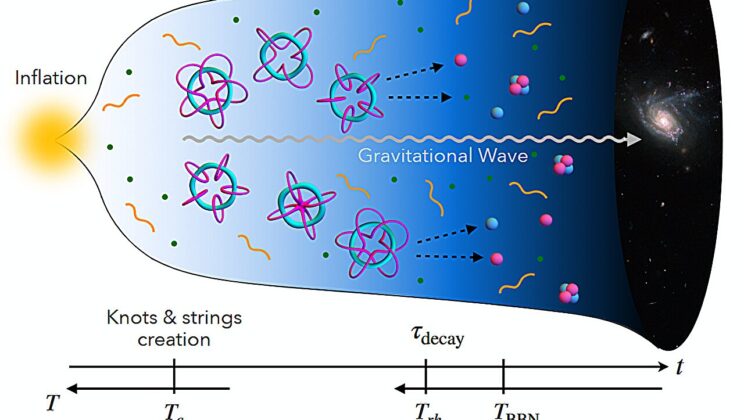
Physicists Say the Universe May Have Begun With Knots — and They Might Explain Why Anything Exists at All
In 1867, Lord Kelvin proposed a picture of atoms that now sounds almost mythic. He imagined that atoms were not…
1,500 Stellar Ghosts Tell the Untold Story of the Milky Way
When a star nears the end of its life, it does not simply fade into darkness. Instead, it performs one…
This Toxic Red River in Spain Could Reveal Whether Mars Was Ever Alive
Sometimes, the greatest stories of planets are written in their smallest grains. Buried in ancient rocks, dissolved in acidic waters,…
They Thought It Was Just an Old Well — Then Archaeologists Found a Mass Grave of Roman Warriors
In the heart of modern-day Osijek, Croatia, archaeologists have uncovered a haunting remnant of Rome’s turbulent past—an ancient water well…
Scientists Solved a 3,500-Year-Old Mystery Linking a Greek Volcano to the Pharaohs
More than 3,500 years ago, the tranquil island of Thera—now known as Santorini—was shattered by one of the most powerful…
Archaeologists Uncover Massive Ancient “Power Pole” That Once Linked Heaven and Earth in Lost American City
Long before the rise of skyscrapers and concrete cities, in the green expanse of the Mississippi Valley, a civilization flourished…
Astronomers Capture the Sharpest-Ever View of a Star’s Disk — And It’s Shockingly Lopsided
In the grand story of astronomy, every breakthrough begins with a new way of seeing. For centuries, humankind has turned…