The universe we see—the stars, the planets, the glowing clouds of gas—represents only a tiny fraction of all that exists.…
Scientists May Have Just Found Proof That Dark Matter Is Destroying Itself at the Center of the Milky Way
For decades, astronomers have been haunted by an invisible presence—an unseen mass that holds galaxies together, bends light from distant…
Can a Gene From People Who Live to 100 Help Kids With Progeria Live Longer? New Study Says Yes
For children born with Hutchinson-Gilford progeria syndrome (HGPS), time is an unforgiving companion. Their tiny bodies age at an astonishing…
Scientists Discover the ‘Perfect Pair’ for Fighting Inflammation — It’s Not Just Omega-3s!
In a world where shelves overflow with supplements promising stronger immunity, sharper minds, and longer lives, a groundbreaking study from…
Scientists Discover How Your Brain Knows When You’ve Had Enough Water — Before Your Body Does
Every moment of our lives, our bodies are engaged in a delicate balancing act. We breathe, eat, drink, and sleep—all…
Social Media May Be Quietly Rewiring Your Child’s Brain, Study Warns
In the past decade, childhood has changed in ways our ancestors could never have imagined. Playgrounds are quieter, conversations shorter,…
Can a Gut Bacteria Transplant Cure Depression? Scientists Say the Answer Might Be Yes
Depression is not just a passing sadness—it is one of humanity’s most pervasive and painful conditions, affecting over 280 million…
Scientists Create “Water-Loving” Glowing Molecules That Could Revolutionize Disease Detection
In a quiet corner of southern Spain, inside the laboratories of the University of Malaga, a team of chemists has…
Astronomers Spot ‘Little Red Dots’ at the Edge of Time — And They Could Be the Universe’s First Black Holes
When the James Webb Space Telescope (JWST) opened its golden mirrors to the cosmos in 2022, humanity’s view of the…
Scientists Are Teaching Robots to Drive on the Moon—And It’s Changing Space Travel Forever
The Moon has always been a symbol of human curiosity—a distant world shimmering in our night sky, calling explorers to…
Scientists Uncover Mysterious “Brain Cleaning Waves” That Happen Only in Deep Sleep
Every night, as we drift into slumber, our brains enter a remarkable state of restoration and renewal. While our bodies…
Scientists Discover Fat Molecules Secretly Guide the Body’s Killer Immune Cells
When the immune system goes to war, it does so with extraordinary precision. Each strike must be accurate—too weak, and…
Astronomers Found a Cosmic Explosion That Lasted a Whole Day—And It Shouldn’t Be Possible
The universe, vast and ancient beyond imagination, still finds ways to astonish us. For every new telescope we build, every…
The Secret Compass in a Bat’s Brain Could Explain How Humans Navigate the World
Forty kilometers off the coast of Tanzania lies a lonely speck of land called Latham Island—a rocky, wind-battered outcrop barely…
Scientists Stunned as Giant Manta Rays Dive Over 1,200 Meters Deep—But Not to Hunt or Hide
Far beneath the glimmering surface of the ocean lies a world of quiet darkness, immense pressure, and mystery. It is…
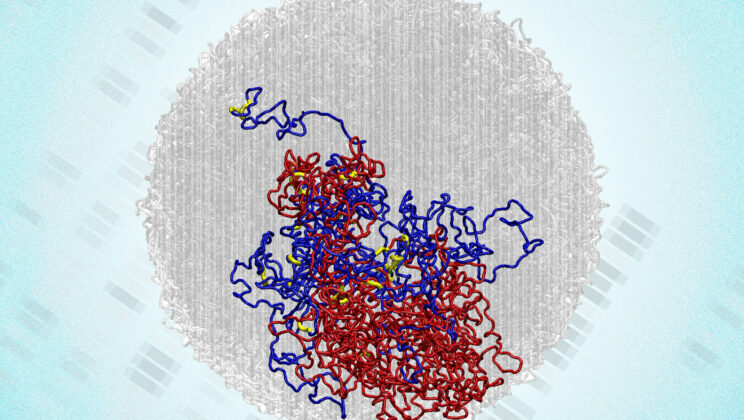
Scientists Shatter a 50-Year Myth: The Genome Never Truly “Resets” During Cell Division
Cell division—known scientifically as mitosis—is one of life’s most crucial events. Every time a cell divides, it must perfectly copy…
This New Discovery Could Change How We Understand the Human Brain—and Artificial Intelligence
Every second of every day, information flows around us—in the digital networks that power our communication, in the neurons that…
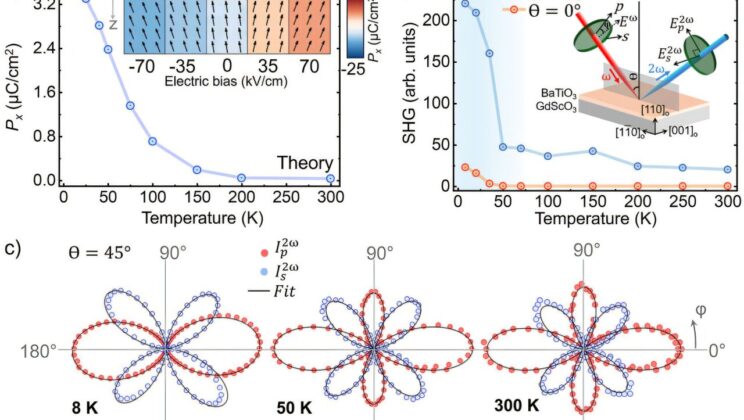
This Classic Material Could Make Data Centers 10x More Efficient—and Change the Internet Forever
In the world of materials science, some stories read like tales of redemption. Barium titanate, a compound discovered in 1941,…
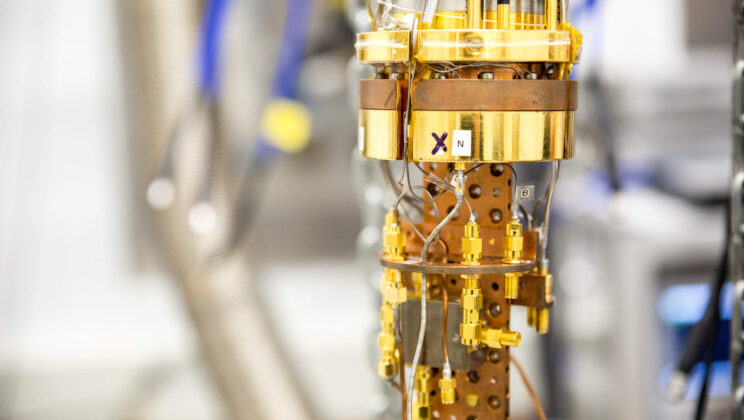
Scientists Connected a “Time Crystal” to the Real World — and It Could Change Quantum Computing Forever
Crystals have always fascinated the human imagination. Their geometric perfection, shimmering colors, and elegant order arise from the precise arrangement…
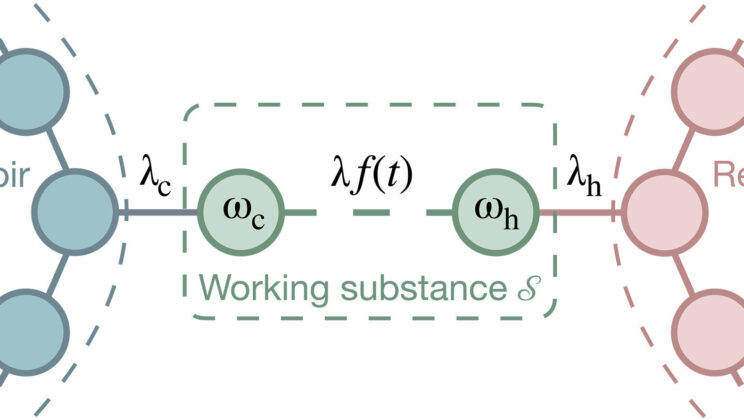
Physicists Shatter 200-Year-Old Law of Thermodynamics — Quantum Engines Could Break Efficiency Limits
For nearly two centuries, the Carnot principle has stood as one of the cornerstones of physics—a law so fundamental that…
Beneath Antarctica’s Waters Lies a Carbon Mystery That Could Change Everything
Far to the south, beyond the reach of continents and crowded cities, lies the Southern Ocean—a vast ring of icy…
This Island’s Coral Skeletons Just Exposed a Lost Earthquake of Unimaginable Power
Sometime between 1381 and 1391, long before Europeans had mapped the Caribbean or written histories of its islands, the sea…