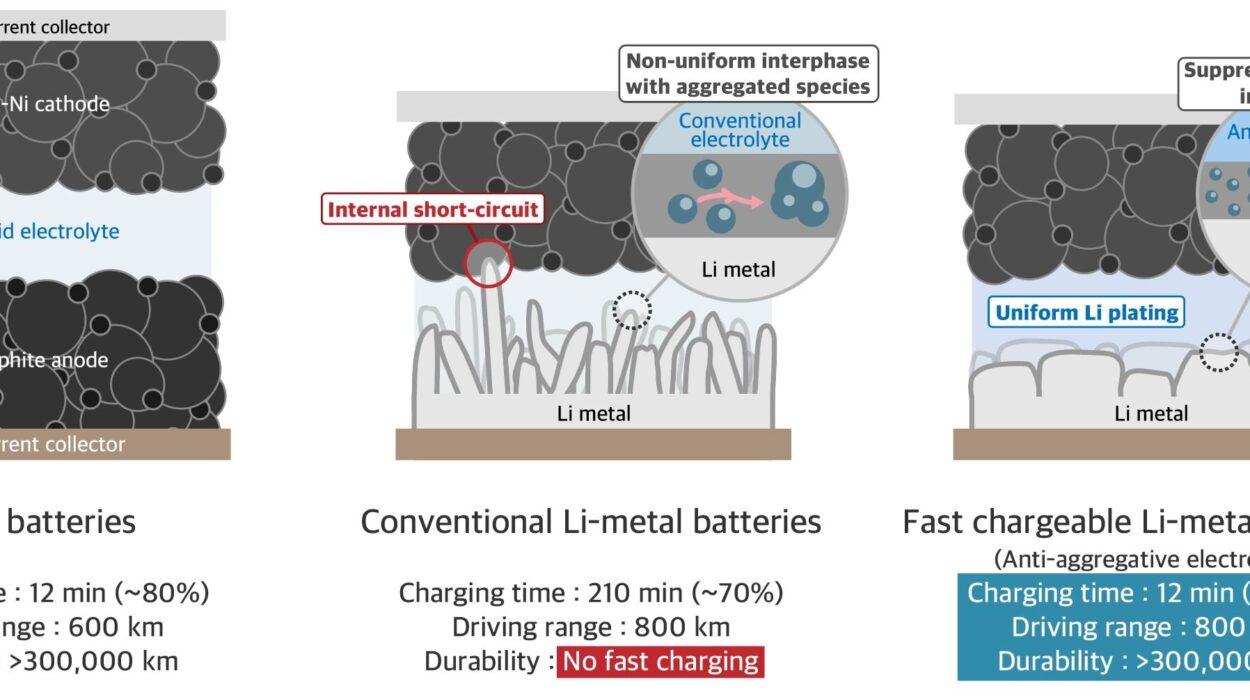
In the quiet hum of a server room, the truth can be hidden in the faintest of digital footprints. To the untrained eye, a cyber attack may seem like a mysterious and invisible act — one moment, the systems are working as intended, and the next, data is missing, ransomware locks the screen, or services grind to a halt. But for a digital forensic investigator, every keystroke, every network request, and every line of code is a potential clue.
Incident forensics is the art and science of retracing the attacker’s steps. It is a discipline where technology meets detective work, where patience is as important as processing power, and where the smallest anomaly can unravel the entire mystery.
When a cyber attack occurs, time is both an enemy and an ally. The longer an attacker has inside a network, the deeper the potential damage. Yet, in those precious minutes and hours after detection, forensic experts must tread carefully. Every move could destroy valuable evidence.
This is where the story begins: with a network under siege, a team of investigators rushing in not with weapons, but with forensic toolkits, deep expertise, and an unyielding commitment to the truth.
Understanding the Nature of the Beast
A cyber attack is rarely a single event. It is usually a sequence of deliberate, calculated steps. Before an attacker ever deploys malicious software or steals data, they have already scouted their target. This reconnaissance phase — invisible to most — leaves faint traces: unusual login attempts, subtle probes against network ports, or web traffic patterns that don’t quite belong.
In incident forensics, understanding the attacker’s motive is as important as understanding their method. Was this a financially motivated ransomware gang? A nation-state seeking sensitive intelligence? A hacktivist group aiming to make a political statement? Each type of adversary has its own signature tactics.
But unlike traditional crime scenes, where fingerprints and footprints may be obvious, the digital realm hides its clues in logs, packet captures, memory dumps, and file metadata. It is a shifting landscape, where evidence can be overwritten in seconds and where an attacker can be halfway across the globe.
Securing the Scene
When forensic experts arrive, their first job is to stabilize the environment. This is not as simple as unplugging machines — doing so can destroy volatile data, like what is stored in RAM, which might hold encryption keys, malicious code in execution, or a record of the attacker’s live commands.
Instead, investigators preserve the scene by making exact copies — forensic images — of hard drives, network data, and memory. These snapshots are preserved under strict chain-of-custody protocols, ensuring that in court or in a security report, there can be no doubt about their integrity.
Just like crime scene tape in the physical world, access controls are established in the digital one. Only authorized personnel can interact with the affected systems. Every action is logged. The integrity of evidence is paramount, because in many cases, these investigations may lead to legal consequences for attackers.
Following the Digital Breadcrumbs
From here, the real detective work begins. A cyber attack is like a trail through a forest: some footprints are deep and obvious, others are faint and easily missed. The forensic expert starts to piece together a timeline — when the intrusion began, how the attacker gained access, and what they did once inside.
Logs are the diary of a system. Authentication logs might reveal a successful login from an unusual location. Firewall logs can show connections to suspicious IP addresses. Application logs may contain traces of unauthorized queries to a database. Even seemingly mundane records — the exact second a process started, the unusual length of time a session lasted — can point toward a larger story.
Network forensics plays an equally vital role. Capturing and analyzing network traffic can reveal command-and-control (C2) communications, where malware “phones home” to an attacker’s server for instructions. By dissecting packets, investigators can see data exfiltration in progress or spot hidden malware downloads masquerading as legitimate web requests.
Unmasking the Tools of the Trade
No two cyber attacks are identical, but many use recognizable components. Malware often leaves behind distinct code patterns, file hashes, or encryption methods that can be matched against known samples in global threat intelligence databases.
Reverse engineering malicious code is one of the most challenging — and rewarding — parts of incident forensics. By deconstructing the malware, analysts can learn not only what it does, but also how it does it, and sometimes even where it came from. Was it built using a known exploit kit sold on the dark web? Was its command server hosted in a country notorious for harboring cybercriminal groups? Does its code reuse functions from a previous, high-profile attack?
Each discovery brings the investigation closer to answering the two central questions: Who did this? And how can we stop them from doing it again?
The Human Factor
One of the most surprising truths in incident forensics is that attackers often exploit human weaknesses more than technical ones. Phishing emails remain one of the most common entry points. An employee clicking on a seemingly harmless attachment can open the door for an entire ransomware network lockdown.
Forensic experts must therefore investigate not only the technical systems but also the social engineering aspect of the attack. Was the phishing email part of a larger, targeted spear-phishing campaign? Did the attacker impersonate a trusted vendor or a company executive? What psychological levers did they pull to gain trust?
By understanding these human vulnerabilities, organizations can better prepare their employees — often their weakest link — to recognize and resist such attacks.
The Race Against Time
Digital evidence is fragile. Logs can roll over, overwriting older entries. Attackers can deploy “anti-forensics” tools to wipe traces of their activities. Cloud environments present additional challenges, as evidence may be distributed across multiple physical locations, each with its own retention policies.
Forensic experts work in a race against time, capturing every possible fragment before it vanishes. They use specialized software to recover deleted files, carve data out of unallocated disk space, and extract volatile memory contents before they dissipate.
Each piece of recovered evidence is meticulously documented. Investigators must be able to show, step by step, how the evidence was collected, what it means, and how it supports the conclusions of the investigation.
The Attacker’s Path
A key part of any forensic investigation is mapping the attacker’s path through the network. This is sometimes called “attack chain reconstruction.” By visualizing the attack, investigators can see where the initial breach occurred, how the attacker moved laterally between systems, and what privilege escalations they performed to gain control over critical assets.
In some cases, this map reveals shocking truths. The initial breach may have occurred months before the attack was detected, with the intruder quietly gathering intelligence, creating backdoors, and waiting for the right moment to strike. This is particularly common in advanced persistent threat (APT) campaigns, often attributed to state-sponsored actors.
Understanding the attacker’s journey is essential not only for closing the current breach but also for identifying long-term security improvements.
The Power of Collaboration
Incident forensics is rarely a solo effort. It is a team sport that draws on multiple disciplines: malware analysts, network engineers, threat intelligence specialists, cloud architects, and sometimes even law enforcement agents.
Global collaboration is increasingly important. Attackers operate across borders, and so must the defenders. International organizations like INTERPOL and private cybersecurity firms share threat data, malware samples, and indicators of compromise (IOCs) to help others recognize and defend against similar attacks.
Forensic reports often feed into global threat intelligence databases, turning one organization’s painful breach into another’s early warning system.
Lessons Learned and the Road Ahead
When the investigation is complete, the work is far from over. A comprehensive post-incident report lays out the timeline, the attacker’s methods, the damage done, and the recommendations for future defenses.
Forensic experts know that no system can be made completely impenetrable. The goal is resilience: to detect attacks faster, respond more effectively, and recover more quickly.
Cyber attacks are evolving. Artificial intelligence, deepfake technology, and quantum computing will bring new challenges. But so too will forensic science evolve, with more powerful tools, automated threat correlation, and AI-assisted anomaly detection.
In the end, incident forensics is not just about catching the perpetrator. It is about understanding the attack so deeply that the organization emerges stronger than before — more aware, more prepared, and more determined to protect the digital spaces in which we now live our lives.
The Human Drive to Seek the Truth
Perhaps the most compelling part of incident forensics is not the technology but the mindset. Investigators are driven by a relentless curiosity, a refusal to accept the unknown. They work long hours in front of glowing screens, parsing endless lines of logs, chasing down the meaning of a single suspicious process ID.
In their work, they see the best and worst of humanity: the creativity of those who seek to protect, and the cunning of those who seek to exploit. Yet, in every case, the mission remains the same — to shine a light into the darkest corners of the digital world, to find the truth, and to turn that truth into action.
In a world where cyber attacks are not a matter of if but when, the forensic investigator is our detective, our archivist, and our storyteller. They are the ones who take the chaos of a breach and craft from it a clear narrative: this is what happened, this is how it happened, and this is how we will stop it from happening again.